Back in 2016, the Android community reeled from an exploit called Drammer. Drammer rooted your device by exploiting a vulnerability. Google quickly patched the vulnerability, temporarily mitigating the attack. Unfortunately, Google’s fix worked for 21 months, but now we’ve seen a similar attack take place under the name RAMpage.
Both Drammer and the newly unveiled RAMpage use a “Rowhammer” exploit to root your Android device.
Rowhammer is a class of exploit that changes data stored in memory chips. To change that data, the exploits will repeatedly access the internal rows of that memory, which is where individual bits are stored. The attacks will “hammer” the rows thousands of times a second, eventually causing the bits to flip, changing the 0s to 1s and vice versa.
We’ve seen Rowhammer attacks take place against PCs, making it possible for untrusted computer software to gain full system privileges and even bypass security sandboxes. A later variation of the attack allowed infected websites to conduct Rowhammer attacks through JavaScript.
Then, Rowhammer attacks migrated to Android devices. In 2016, “Drammer” was spotted attacking Androids using similar attack methods to the ones used against PCs.
Google temporarily mitigated Rowhammer attacks against Android by changing Android’s ION memory manager, “restricting access to physical contiguous kernel memory,” as explained by ArsTechnica.
Google’s fix wasn’t meant to be temporary. Unfortunately, a new exploit called RAMpage has resurfaced that uses Rowhammer-like strategies to root Android.
“Every Mobile Phone Since 2012” is Affected by RAMpage
RAMpage was discovered by Victor Van der Veen, a professor at Vrije Universiteit Amsterdam who published his research in a blog post last Wednesday.
Van der Veen and his colleagues report that RAMpage can affect virtually any modern mobile device, including phones and tablets.
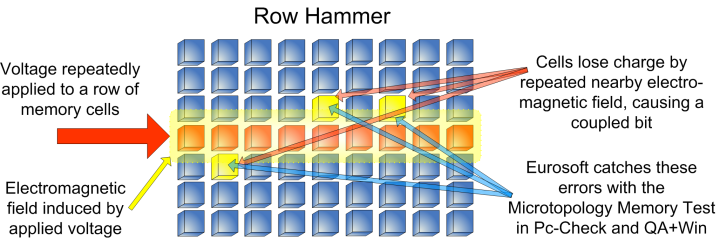
Photo courtesy of Euro Soft UK
In fact, “every [Android-based] mobile device that is shipped with LPDDR2, LPDDR3, or LPDDR4 memory is potentially affected [by RAMpage], which is effectively every mobile phone since 2012.”
Van der Veen and his colleagues tested the exploit on a number of devices. They were able to successfully achieve Rowhammer attacks (bit flips) on the Nexus 5, Nexus 4, and the Google Pixel 1. All three devices use different types of RAM, (LPDDR2, LPDDR3, or LPDDR4), indicating the exploit works regardless of the physical RAM used.
Van der Veen published the results of his research here.
Large-Scale Rooting Attacks Are Unlikely
Any time a large number of devices are affected by an exploit, it opens the opportunity for large-scale attacks.
Fortunately, Van der Veen claims large-scale attacks with Rowhammer are unlikely. Google echoed his sentiment, and a Google spokesman has released a statement regarding the company’s official stance:
“We have worked closely with the team from Vrije Universiteit, and though this vulnerability isn’t a practical concern for the overwhelming majority of users, we appreciate any effort to protect them and advance the field of security research. While we recognize the theoretical proof of concept from the researchers, we are not aware of any exploit against Android devices.”
Google also added that new devices have Rowhammer-specific protections in place. So while the exploit might affect devices made since 2012, it may not affect devices made in 2018 onward.
In any case, RAMpage is one of the few Android-based exploits that could root your device and cause serious damage. Fortunately, it doesn’t appear to pose a major security threat to Android users at this time.
