If you’re the type of person who regularly downloads Android apps from outside the Google Play Store, then you should be extra careful over the next few weeks. A recently-discovered Android adware virus has been discovered in over 20,000 Android apps downloaded from third-party online app stores.
That adware automatically roots your Android after installation, then lodges itself deep within your directory files.
It works by masquerading itself as a system application.
That might not mean much to you, but it’s actually really important to how the virus works: because it’s a system application, the virus stays on your device even after a factory reset.
In other words, you’re going to have this virus on your device for a while if you get infected. It’s nearly impossible to remove.
The virus was discovered by Android security watchdog Lookout, which claims to have found over 20,000 samples of Trojanized apps in the wild.
Infected Apps Are Fully Functional And Appear Normal
The biggest problem with this adware is that many users are unaware they’ve been infected.
The Trojanized apps appear to be fully functional copies of the original apps they’re meant to replicate.
The only real difference is that the apps also contain a devastating auto-root adware deep within their files. That’s a pretty big difference.
Some of the apps infected by this new adware include WhatsApp, SnapChat, Candy Crush, Google Now, and Okta.
If you’ve downloaded any of these apps from sources outside the Google Play Store, ten your device might be infected.
New Adware Goes by Multiple Names
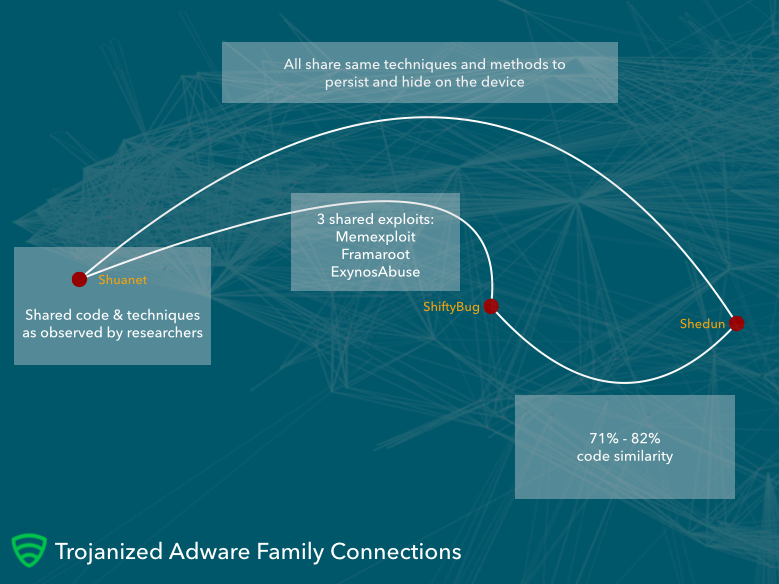
In a blog post on the topic, Lookout claims that the adware goes by multiple names. Lookout actually claimed that there were three different “families” of adware apps, including:
-Shuanet
-Kemoge (also known as ShiftyBug)
-Shudun (also known as GhostPush)
Infected users have been identified around the world, including in the United States, Germany, Russia, India, Jamaica, Sudan, Brazil, Mexico, Iran, and Indonesia.
It’s Not Going Away Anytime Soon
Lookout concluded their depressing blog post with a pessimistic statement about the future:
“We expect this class of trojanized adware to continue gaining sophistication over time, leveraging its root privilege to further exploit user devices, allow additional malware to gain read or write privileges in the system directory, and better hide evidence of its presence and activities.”
Be Extra Careful, Download from the Google Play Store Wherever Possible, and Wait for a Fix
If you only download from the Google Play Store, then you’re not at risk of this infection (as of yet). Researchers claim that the 20,000 apps are all found outside the Play Store.
Obviously, a large number of Android users – especially those in developing countries – are forced to use third party app stores because they don’t have access to the Google Play Store.
If you’re one of those users, then be extra careful when downloading apps online over the next few weeks.
If you’ve already been infected, try to perform a factory data reset. If that doesn’t work, then your best bet is to wait until a major antivirus company releases a certified fix.
