Over the past week, dozens of celebrity nudes have leaked online.
Some people are blaming the hackers who spread and shared the photos, while other people are blaming the celebrities for taking pictures of themselves in the first place.
But really, the only person to blame here is Apple, which has a long history of poor security and unpatched exploits.
Grab your baseball bat and head to the orchard because we’re about to do some Apple bashing. Here are 5 reasons why Apple should be blamed for the latest iCloud photo leak:
5) iOS uploads photos to iCloud by default
Most cloud services request your permission before uploading your photos to the cloud. That’s good, because most people don’t want every picture they’ve ever taken to be uploaded to the internet.
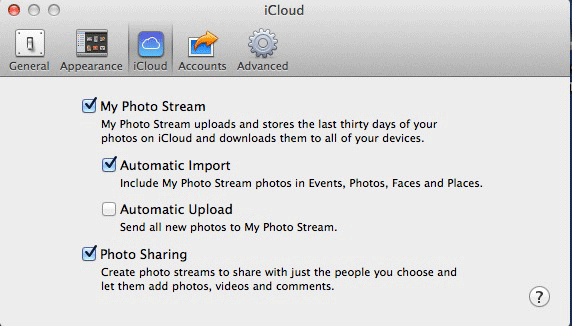
Apple, however, takes a different approach. It wants its users to use iCloud so badly that it automatically enables iCloud photo upload by default on all iPhones and iPads.
Cloud storage has been forced on all of us over the past few years. But no company has forced cloud storage on its users as badly as Apple.
In fact, even the American Civil Liberties Union is concerned about Apple’s automatic Camera Roll to iCloud uploads.
Anyways, every single one of the celebrity photo leaks could have been avoided if the photos weren’t uploaded to iCloud.
Some of these celebrities knew their photos were being automatically uploaded to the internet, but many did not.
4) Because Apple sells itself as the world’s safest operating system
Ten years ago, Apple erroneously claimed that its computers didn’t get viruses. That claim was removed from the Apple store a few years ago because Apple didn’t want to get sued.

Now, Apple is attacking Android for its “toxic hellstew” of vulnerabilities. At the same time, Apple is promoting itself as a bastion of security in a crowded smartphone market.
Ultimately, Apple can make whatever marketing claims it wants to make. However, the real victims here are users, who mistakenly believe everything they do on their phones is protected by this mythical Apple force field.
Apple’s marketing has sold a lot of phones, but it’s also tricked users into thinking they’re more secure than they actually are.
3) The “hack” was so simple it barely deserves to be called a hack
In the early days of the internet, people didn’t care about security very much. Online accounts would let you have as many login accounts as you wanted without ever locking you out.
That was way back in the 1990s and early 2000s. Eventually, people realized that you could easily write a script that tries every password combination in the world until one eventually works.
As a result, companies started implementing “lock outs” after you tried to unsuccessfully login a few times in a row. It was an easy fix to a clumsy hack.
Apple locks users out on some of its services, but not all. Find My iPhone and iCloud both let users try an unlimited number of passwords without ever locking them out.
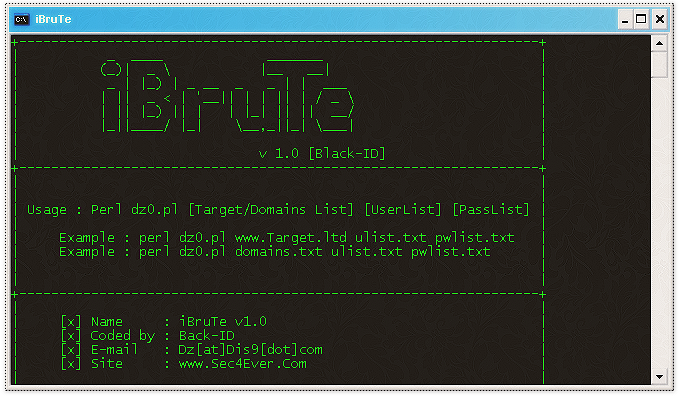
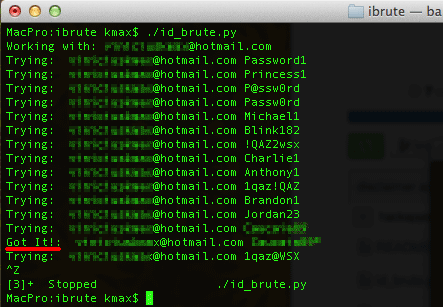
That’s how this hack may have worked: “hackers” used a software program called iBrute to try every password combination on celebrity email accounts. Eventually, one worked and the hacker was instantly given access to the celebrity’s account.
Apple has now fixed the exploit and will lock users out after multiple incorrect login attempts. But obviously, the damage has already been done.
2) Apple is mysteriously against two factor authentication
Over the past three years, major online services like Facebook and Google have begun to offer two factor authentication.
Two factor authentication involves typing in your password and then receiving a second password on your mobile device or email account.
It’s a second layer of protection between yourself and a hacker. Instead of simply guessing your password, the hacker also needs your mobile phone or email account.
It doesn’t make hacking impossible, but it’s a strong deterrent. Today, millions of people around the world use two factor authentication.
Apple, for some mysterious reason, has continuously refused to promote two-factor authentication on its devices.
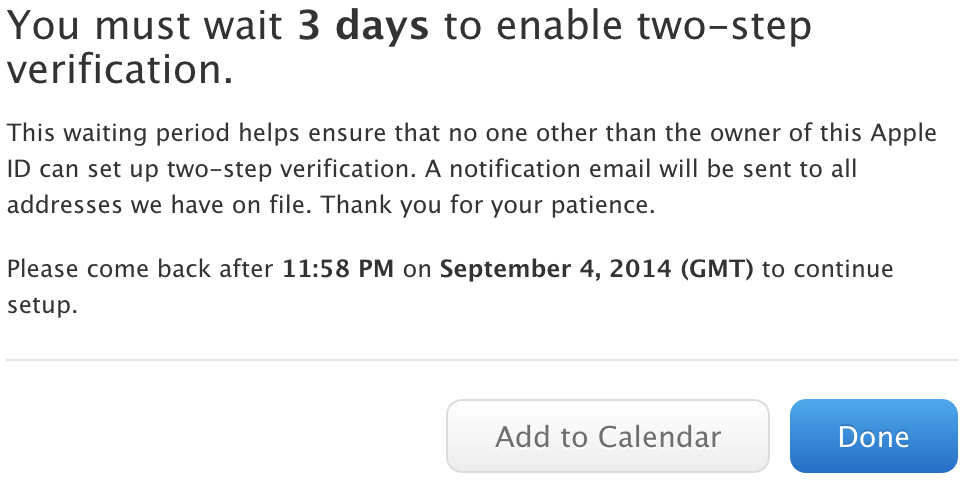
It is possible to get two-factor authentication on your Apple device, but it’s stupidly difficult. Check out this article on DailyDot which walks through the baffling process users are expected to go through in order to enable two-factor authentication. It takes three days to enable. And that article was written after the latest leaks occurred.
The craziest thing is that Apple’s two-factor authentication wouldn’t have even helped in this case, because Apple currently only uses it to protect credit card data – nothing else!
1) The exploit has been publically known and accessible since May 2014
Companies like Google and Windows aren’t perfect. But when someone discovers a major security flaw in their platforms, both companies spring into action and release a patch within days – if not hours of discovery.
Apple, however, takes a different approach and seemingly doesn’t care about protecting its users. The Flashback exploit, for example, was left unpatched for months – even though the fix was relatively straightforward. As a result, 600,000 Mac users were infected by Flashback.
This latest exploit was first publically released onto the internet in May 2014 – and it likely existed for months or even years before that point.
In May, a Russian hacking group released something called iBrute, which was specifically designed to exploit the vulnerability. Since iCloud accounts had no limit on login attempts, iBrute simply tried every password combination until one finally worked.
The exploit was publically released in May 2014. Apple patched the problem on September 1, 2014 – days after dozens of celebrity nudes were leaked online.
It’s 2014 and Apple’s lazy, uncaring approach to customer security is no longer acceptable.
